There are still a lot of companies which still working with Hybrid environments. Some of you might already faced issues that devices states in Pending registration status. For such cases i reworked the way to automatically fix the issue using Intune Remediation
First of all you have to prepare an Entra ID/ Azure dynamic group to collect all devices with Pending Status:
(device.deviceTrustType -eq "ServerAD") and (device.profileType -ne "RegisteredDevice") and (device.accountEnabled -eq True)
When you have collected affected devices you can start of creating the Remediation policy in Intune
At first you have to prepare detection to be sure that device is not in Autopilot Hybrid domain join process, or is not the object within Azure group which wasn’t removed yet from membership.
To figure out if Device isn’t within Autopilot process i’m checking for Successful ODJ blob, which is removed from events on device after around 24 hours from successful Autopilot enrollment.
The hardest part was to convert “dsregcmd /status” to useful for that script.
Detection Script:
###################################################################################################################
# Detection if device is HAADJ registered to solve an issues on devices with HAADJ Pending registration status #
###################################################################################################################
#Checking autopilot event
$filter111 = @{
LogName = 'Microsoft-Windows-DeviceManagement-Enterprise-Diagnostics-Provider/Admin'
Id = '111' # Successfully applied ODJ blob
}
#get autopilot event
$events111 = Get-WinEvent -FilterHashtable $filter111 -MaxEvents 1 -EA SilentlyContinue
$Dsregcmd = New-Object PSObject ; Dsregcmd /status | Where-Object {$_ -match ' : '}|ForEach-Object {$Item = $_.Trim() -split '\s:\s'; $Dsregcmd|Add-Member -MemberType NoteProperty -Name $($Item[0] -replace '[:\s]','') -Value $Item[1] -EA SilentlyContinue}
#check autopilot event
if($events111 -eq $null)
{
#There Is no ODJ join events detected
if (($dsregcmd.AzureADJoined) -notmatch "YES" -or (($dsregcmd.DeviceAuthStatus) -notmatch "SUCCESS")) {
Write-Output "Computer is NOT correctly Hybrid registered fix required" "AzureADJoined Status equals " $dsregcmd.AzureADJoined "DeviceAuth Status Equals " $dsregcmd.DeviceAuthStatus
Exit 1
}
else {
Write-output "No issues detected" "AzureADJoined Status equals:" $dsregcmd.AzureADJoined "DeviceAuth Status Equals:" $dsregcmd.DeviceAuthStatus
Exit 0
}
}
#check autopilot event
elseif($events111 -ne $null)
{
Write-Host "Device Enrollment in process Fix not required"
Exit 0
}
Stop-Transcript
In case if device hybrid object is correctly registered, script will exit with success exit code. Otherwise it will perform remediation.
As first point remediation will unjoin object trough “dsregcmd /leave /debug” command, then certificates will be removed
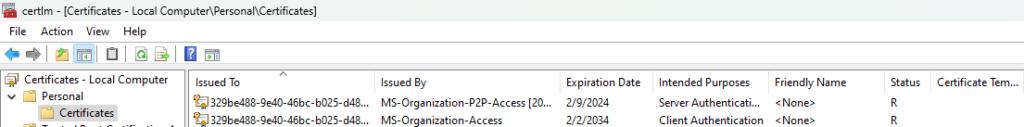
Without that device will not perform clean reregistration. Device have to have connection with DC to request new certificates, when certificates will be applied, script will perform rejoin trough running scheduled task “Automatic-Device-Join” The loop will try to perform rejoin for 60 minutes due the fact that by default AD-Connect sync is running in 30minuts period. You can change that time if you have customized AD-Connect sync interval or small amount of Domain controllers. When device has been successfully registered trough remediation device reboot is not required.
Remediation Script:
<#
.SYNOPSIS
Proactive Remediation for Fixing Hybrid Azure AD join registration
.Description
This is Remediation script.
It will be performed on devices with detected Hybrid Azure AD join registration problem
- unjoin device from AAD
- cleaning certificates
- performing rejoin
.Notes
#>
Start-Transcript -Append c:\temp\HAADJFIX.log
"Starting fixing Hybrid Azure AD Registration"
Write-host "`n ------------------------------------------------ `n"
$Dsregcmd = New-Object PSObject ; Dsregcmd /status | Where {$_ -match ' : '}|ForEach {$Item = $_.Trim() -split '\s:\s'; $Dsregcmd|Add-Member -MemberType NoteProperty -Name $($Item[0] -replace '[:\s]','') -Value $Item[1] -EA SilentlyContinue}
Write-host "DeviceName" $dsregcmd.DeviceName
Write-host "AzureADJoined:" $dsregcmd.AzureADJoined
Write-host "Auth Status:" $dsregcmd.DeviceAuthStatus
Write-host "`n ------------------------------------------------ `n"
if (($dsregcmd.AzureADJoined) -notmatch "YES" -or (($dsregcmd.DeviceAuthStatus) -notmatch "SUCCESS")) {
Write-host "Computer is NOT correctly Hybrid registered fix required" "AzureADJoined Status equals " $dsregcmd.AzureADJoined "DeviceAuth Status Equals " $dsregcmd.DeviceAuthStatus
"Deregistering Device: $env:computername from Azure `n "
dsregcmd.exe /leave /debug
Write-host "`n ------------------------------------------------ `n"
"Start-Sleep for 10 Seconds `n "
Start-Sleep -Seconds 10
Write-host "`n ------------------------------------------------ `n"
"`n looking for leftover certificates `n "
Get-ChildItem 'Cert:\LocalMachine\My\' | ? { $_.Issuer -match "MS-Organization-Access|MS-Organization-P2P-Access \[\d+\]" } | % {
Write-Host "Removing leftover Hybrid-Join certificate $($_.DnsNameList.Unicode)" -ForegroundColor Cyan
Remove-Item $_.PSPath
}
$Dsregcmd = New-Object PSObject ; Dsregcmd /status | Where {$_ -match ' : '}|ForEach {$Item = $_.Trim() -split '\s:\s'; $Dsregcmd|Add-Member -MemberType NoteProperty -Name $($Item[0] -replace '[:\s]','') -Value $Item[1] -EA SilentlyContinue}
$t = 9
while (!($Dsregcmd.AzureADJoined -match "YES" -and $Dsregcmd.DeviceAuthStatus -match "SUCCESS") -and $t -gt 0 )
{
# join computer to Azure again
"Joining $env:COMPUTERNAME to Azure `n"
Write-Verbose "by running: Get-ScheduledTask -TaskName Automatic-Device-Join | Start-ScheduledTask"
$task = Get-ScheduledTask -TaskName "Automatic-Device-Join"
$task | Start-ScheduledTask
Start-Sleep -Seconds 10
while ($Task.state -ne "Ready") {
Start-Sleep -Seconds 5
"Waiting for sched. task 'Automatic-Device-Join' to complete"
}
Start-Sleep -Seconds 30
$task = Get-ScheduledTask -TaskName "Automatic-Device-Join"
$taskinfo = $task | Get-ScheduledTaskInfo
if ($taskinfo.lasttaskresult -ne 0) {
write-host "Sched. task Automatic-Device-Join failed. Is $env:COMPUTERNAME synchronized to AzureAD?"
}
else
{
write-host "Scheduled task Automatic-Device-Join returned Success code"
}
# check certificates
"Waiting for certificate creation"
$i = 30
Write-Verbose "two certificates should be created in Computer Personal cert. store (issuer: MS-Organization-Access, MS-Organization-P2P-Access [$(Get-Date -Format yyyy)]"
Start-Sleep 3
while (!($hybridJoinCert = Get-ChildItem 'Cert:\LocalMachine\My\' | ? { $_.Issuer -match "MS-Organization-Access|MS-Organization-P2P-Access \[\d+\]" }) -and $i -gt 0) {
Start-Sleep 3
--$i
$i
}
"Certificates created Waiting 30 secunds for status check"
Start-Sleep -Seconds 30
$Dsregcmd = New-Object PSObject ; Dsregcmd /status | Where {$_ -match ' : '}|ForEach {$Item = $_.Trim() -split '\s:\s'; $Dsregcmd|Add-Member -MemberType NoteProperty -Name $($Item[0] -replace '[:\s]','') -Value $Item[1] -EA SilentlyContinue}
Write-host "AzureADJoined:" $dsregcmd.AzureADJoined
Write-host "Auth Status:" $dsregcmd.DeviceAuthStatus
if (($dsregcmd.AzureADJoined) -notmatch "YES" -or (($dsregcmd.DeviceAuthStatus) -notmatch "SUCCESS")) {
Write-Host "Sleep for 5 minutes"
Start-Sleep -Seconds 300
--$t
Write-Host "Possible retries $t"
}
}
# check AzureAd join status
$Dsregcmd = New-Object PSObject ; Dsregcmd /status | Where {$_ -match ' : '}|ForEach {$Item = $_.Trim() -split '\s:\s'; $Dsregcmd|Add-Member -MemberType NoteProperty -Name $($Item[0] -replace '[:\s]','') -Value $Item[1] -EA SilentlyContinue}
Write-host "DeviceName" $dsregcmd.DeviceName
Write-host "AzureADJoined:" $dsregcmd.AzureADJoined
Write-host "Auth Status:" $dsregcmd.DeviceAuthStatus
if ($dsregcmd.AzureADJoined -match "YES") {
++$AzureAdJoined
}
if ($hybridJoinCert -and $AzureAdJoined) {
"$env:COMPUTERNAME was successfully joined to AAD again."
} else {
$problem = @()
if (!$AzureAdJoined) {
$problem += " - computer is not AzureAD joined"
}
if (!$hybridJoinCert) {
$problem += " - certificates weren't created"
}
Write-Error "Join wasn't successful:`n$($problem -join "`n")"
Write-Warning "Check if device $env:COMPUTERNAME exists in AAD"
Write-Warning "Run:`ngpupdate /force /target:computer"
Write-Warning "You can get failure reason via manual join by running:dsregcmd /join /debug"
}
}
else
{
Write-Host "Device is correctly registered no fix required"
}
Stop-Transcript ![]()

Hi Michal,
Long time no seen! When can we expect a new insightful article from you please? 🙂
Best